Create EC2 Instance Connect Endpoint (Optional)
EC2 Instance Connect Endpoint
In step 4.2 test connection, to access EC2 Private you need to:
- Use the pscp tool to copy the key pair from our machine to EC2 Public
- Access EC2 Public
- Grant permission to key pair
- SSH to EC2 Private server
-> As you can see, now EC2 Public acts as Bastion Host and we need to pay for this instance. So is there a way to save costs, reduce configuration steps while still accessing EC2 Private and ensuring security?
On June 13, 2023, AWS launched the EC2 Instance Connect Endpoint (EIC Endpoint) function to help customers access EC2 instances without needing public IP addresses, through the protocol SSH and RDP.
EIC Endpoint replaces Bastion Host, which means eliminating the workload: patching, managing, auditing and the cost of the previous Bastion Host instance. There are no additional costs for EIC Endpoint, however data transfer costs will apply
Architecture description EIC Endpoint
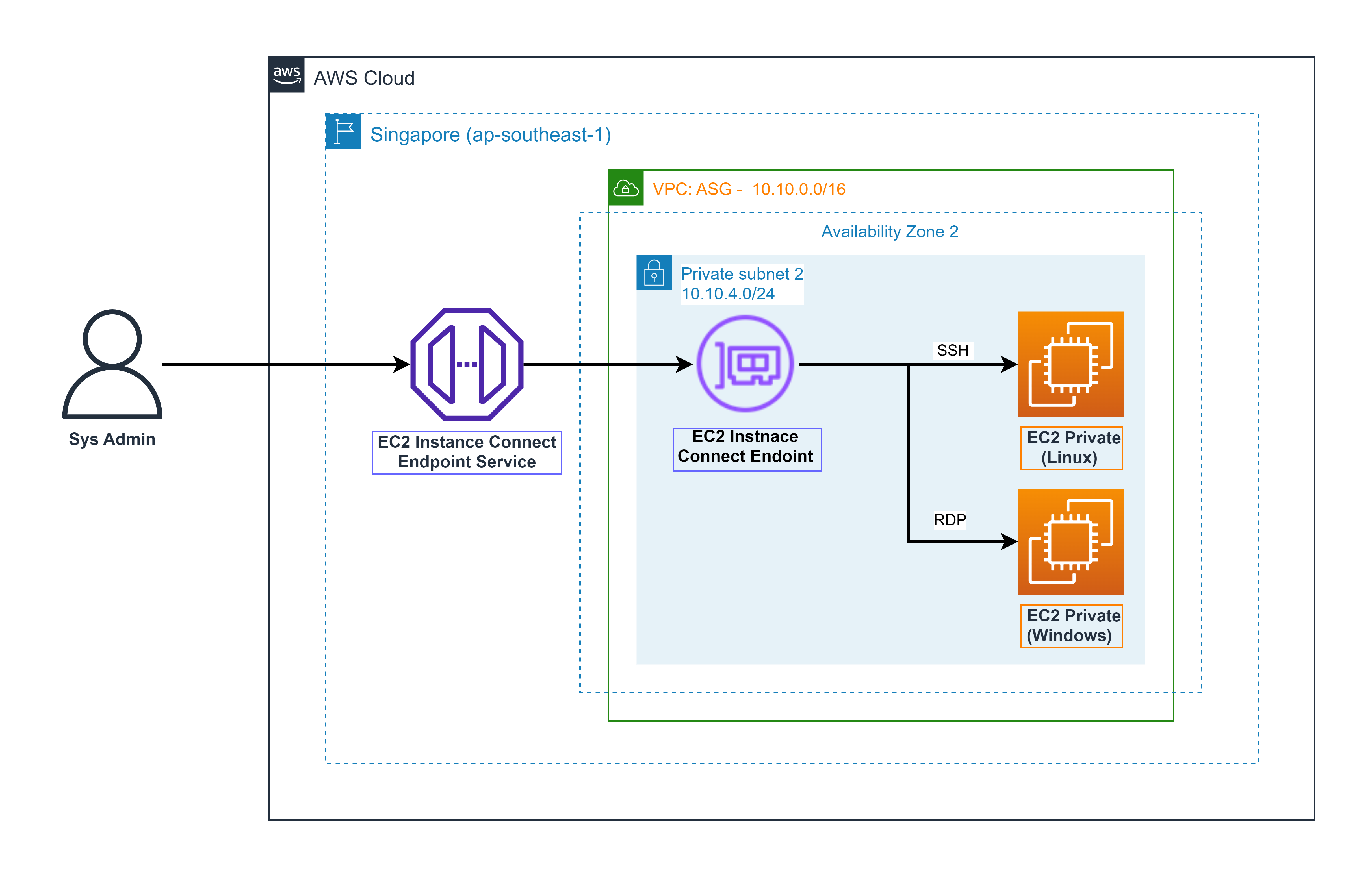
-
Create Security Group for EIC Endpoint
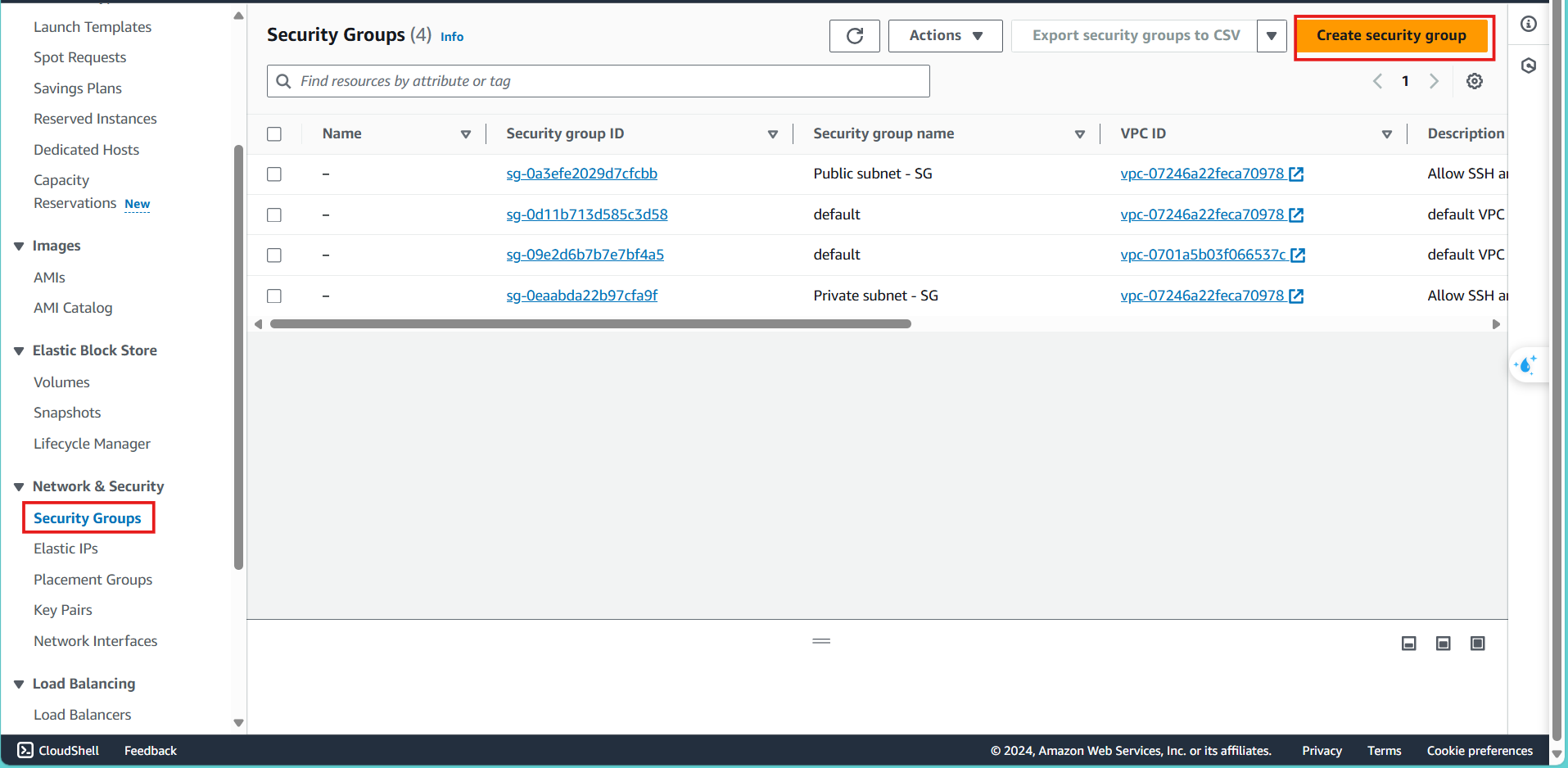
- In the search box, enter: security groups, in the features section select Security groups
- Select Create security group
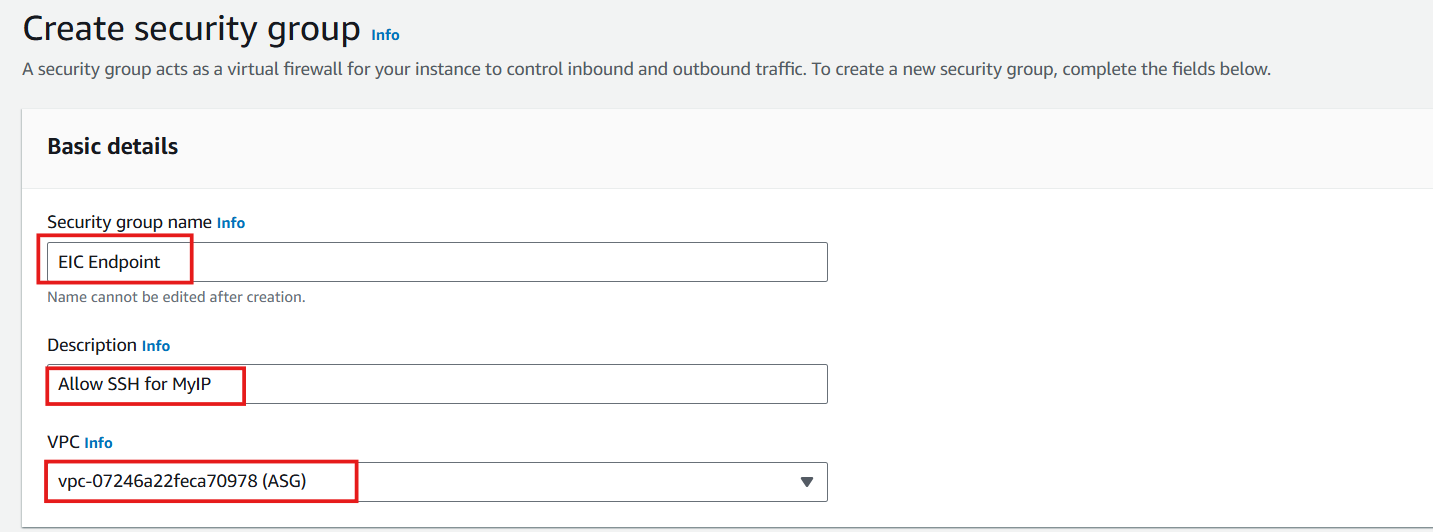
- In the Security group name section, enter
EIC Endpoint - In the Description section, enter
Allow SSH for MyIP - In the VPC section, select ASG VPC
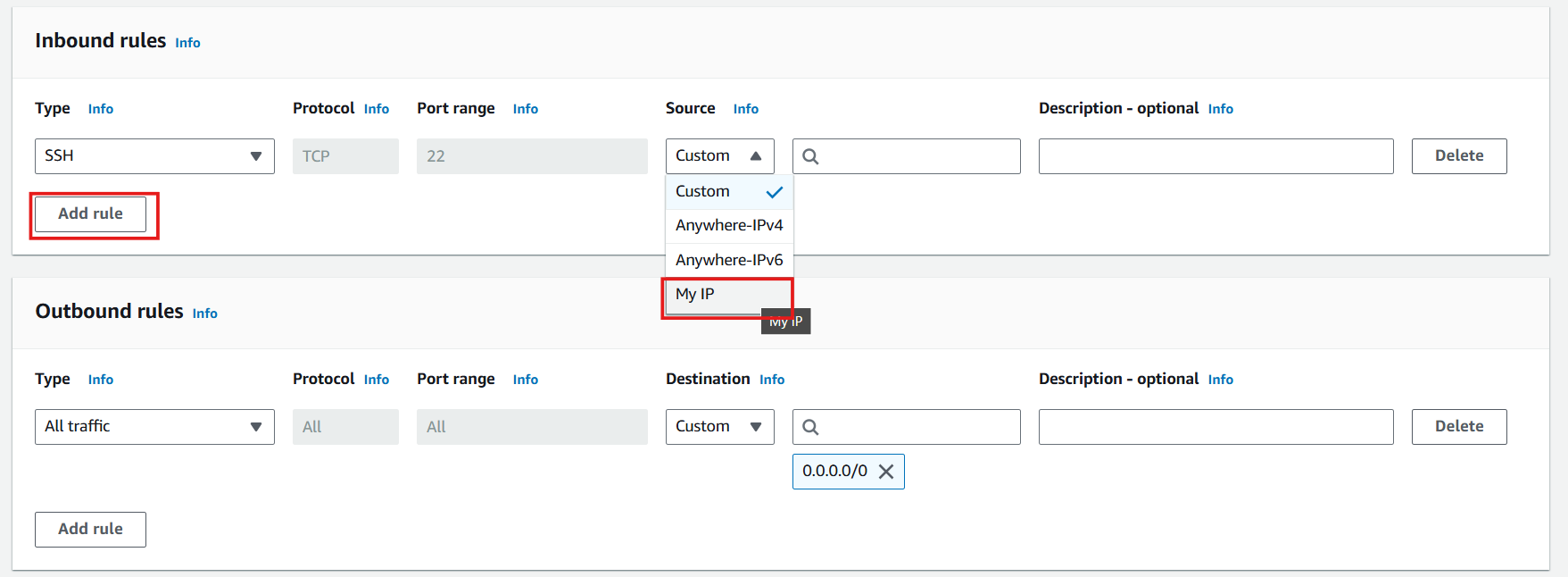
- Select Add rule
- In the Type section, select protocol SSH
- In the Source section, select My IP with the meaning: only allow your IP address with SSH protocol to pass through this Security group
- The remaining values remain the same.
- Select Create security group
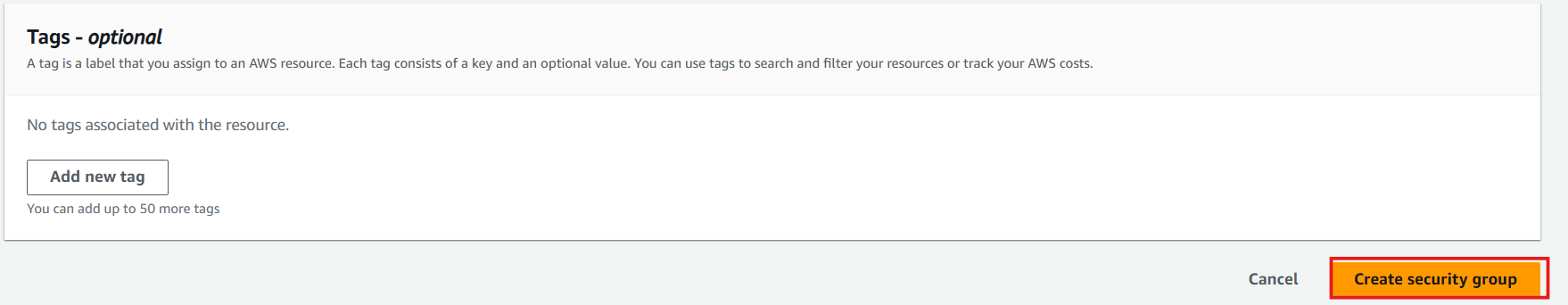
-
Create EC2 Instance Connect Endpoint
-
In the search box, enter:
endpoint services, in the Features section select endpoint services -
Select Create endpoint
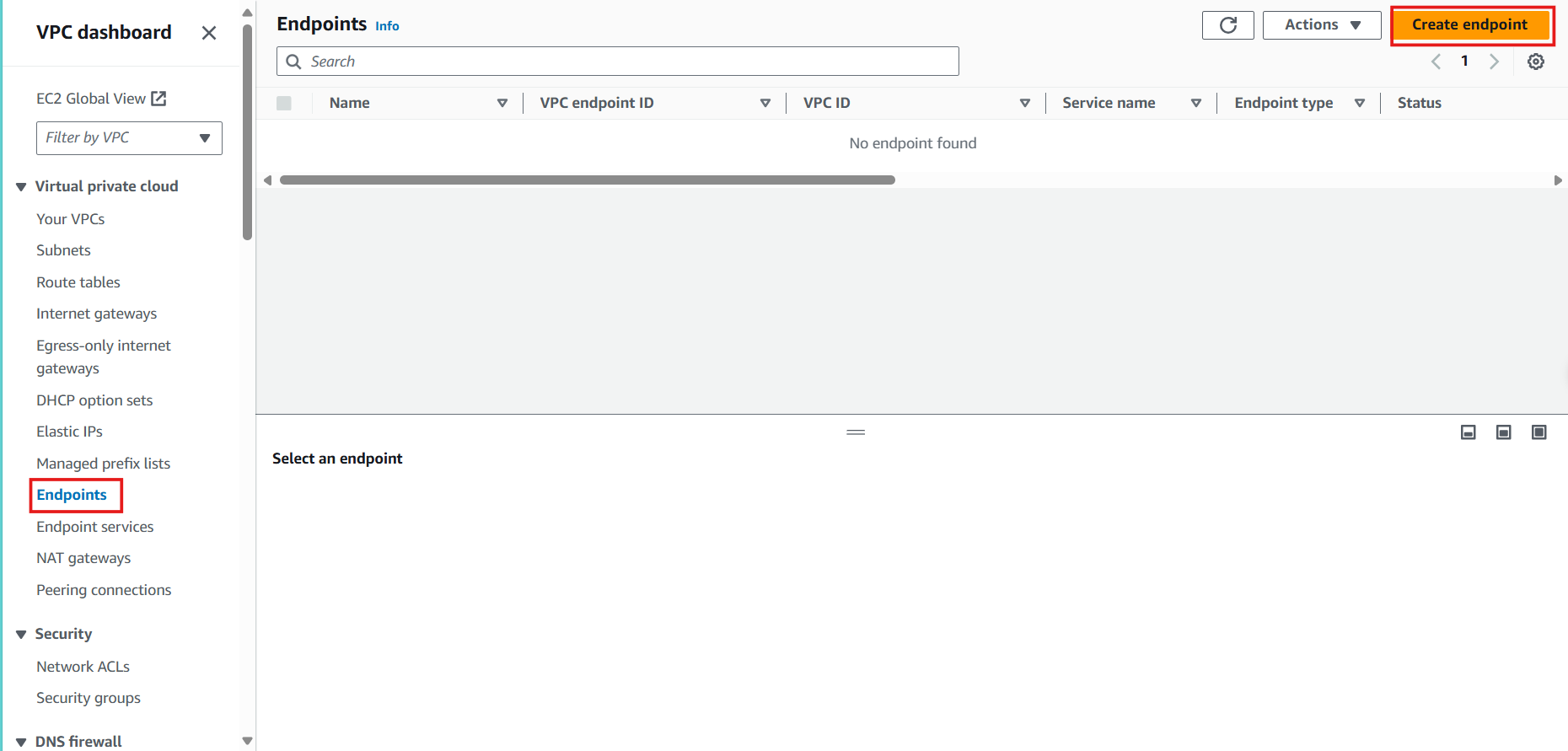
-
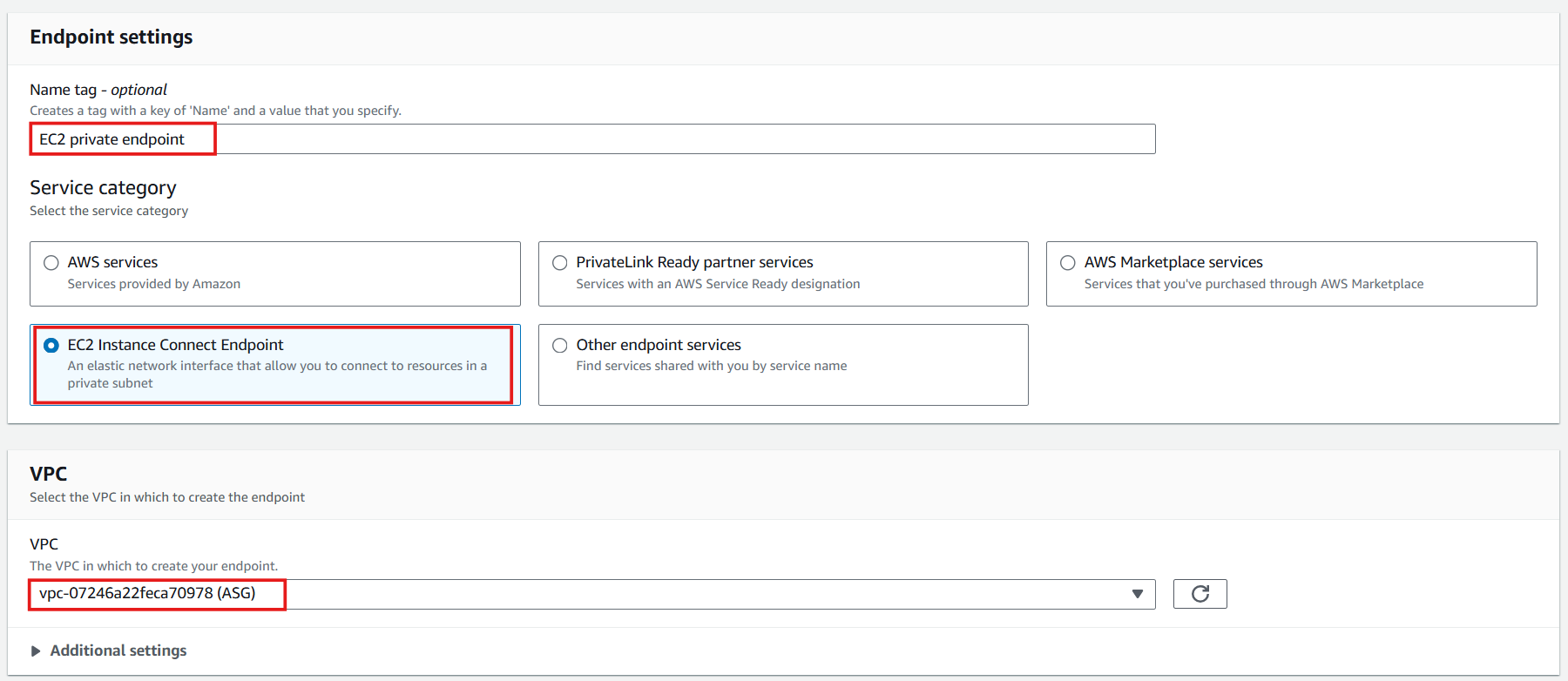
In the Name tag section, enter:
EC2 private endpoint -
In the Service category section, select: EC2 Instance Connect Endpoint
-
In VPC section, select ASG-VPC
-
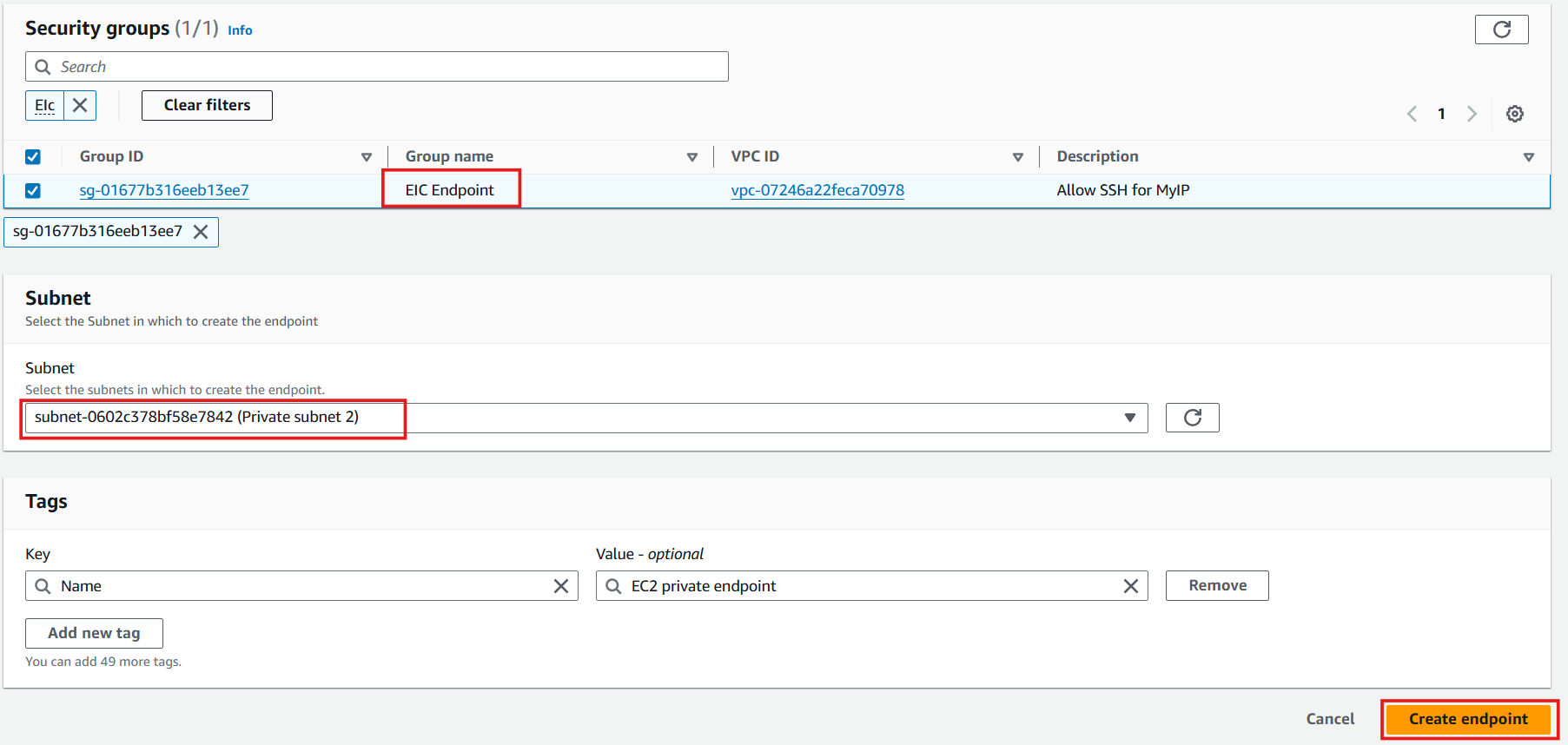
In the Security groups section, select: EIC Endpoint created in step 1
-
In the Subnet section, select: subnet-0da7e5096deb895e1 (Private subnet 2) is the subnet of EC2 Private
-
Select Create endpoint
-
Wait for Status to change to Available and go to the next step
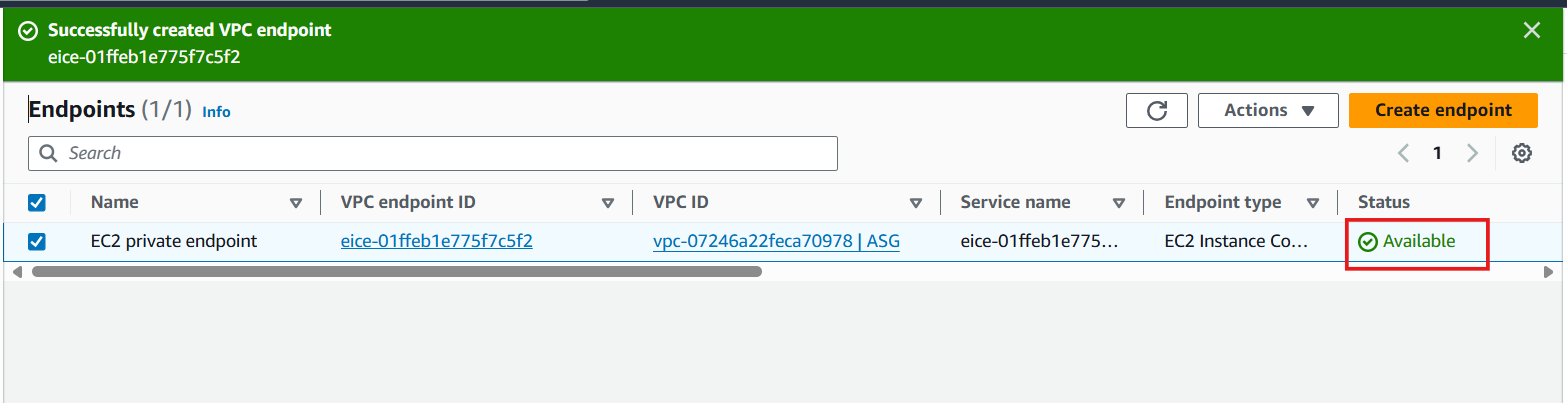
-
-
Access EC2 Private via EC2 Instance Connect Endpoint
-
At the EC2 interface, check the box of EC2 Private
-
In the Public IPv4 address section, check and see: there is no Public IP value - meaning we cannot access this EC2 via Public IP
-
Select Connect
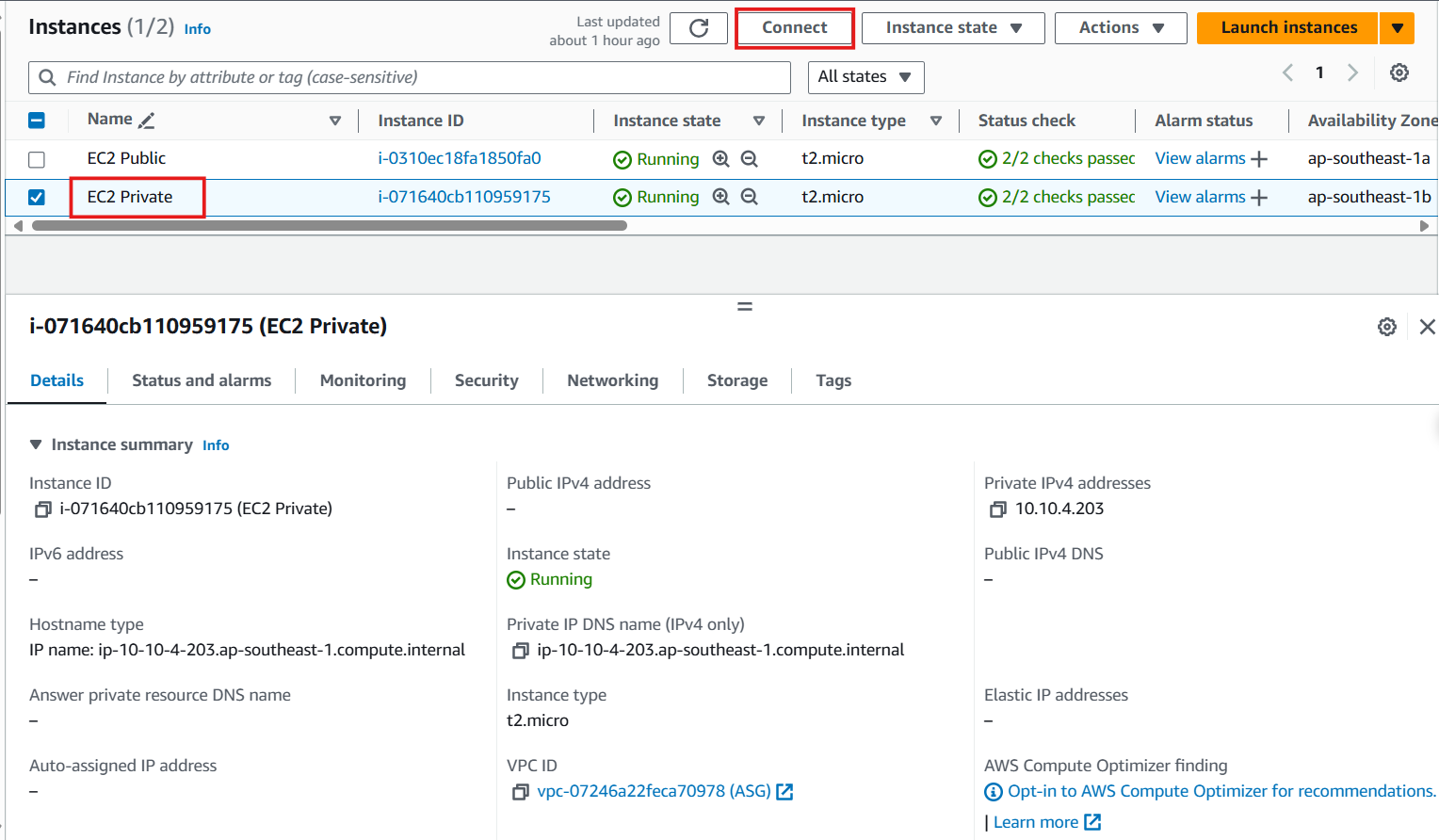
-
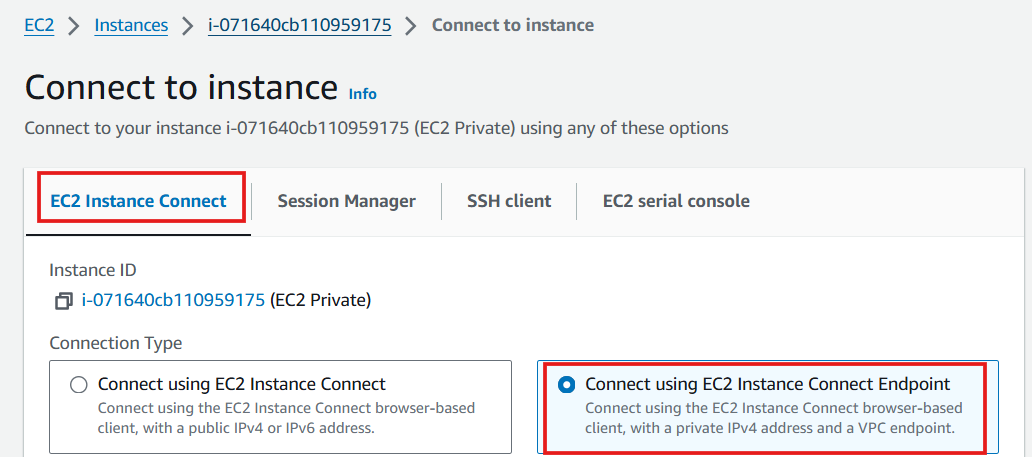
In the Connection Type section, select Connect using EC2 Instance Connect Endpoint
-
In the EC2 Instance Connect Endpoint section, select the EIC just created in step 2
-
Select Connect
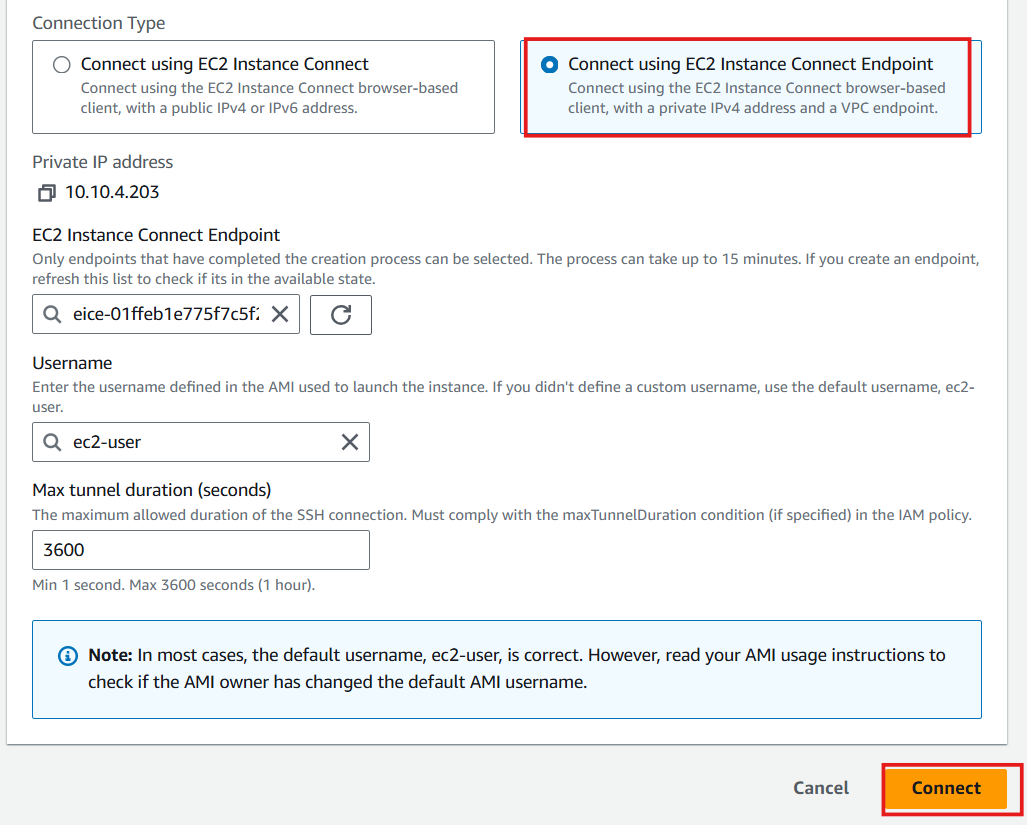
- Congratulations, you have successfully accessed EC2 Private via EC2 Instance Connect Endpoint only from your IP address
Normally, you will do the lab using a user with AdministratorAccess permission . In the opposite case, you need to refer to the documentation to grant the User permission to operate the above steps. IAM permissions to use EC2 Instance Connect Endpoint