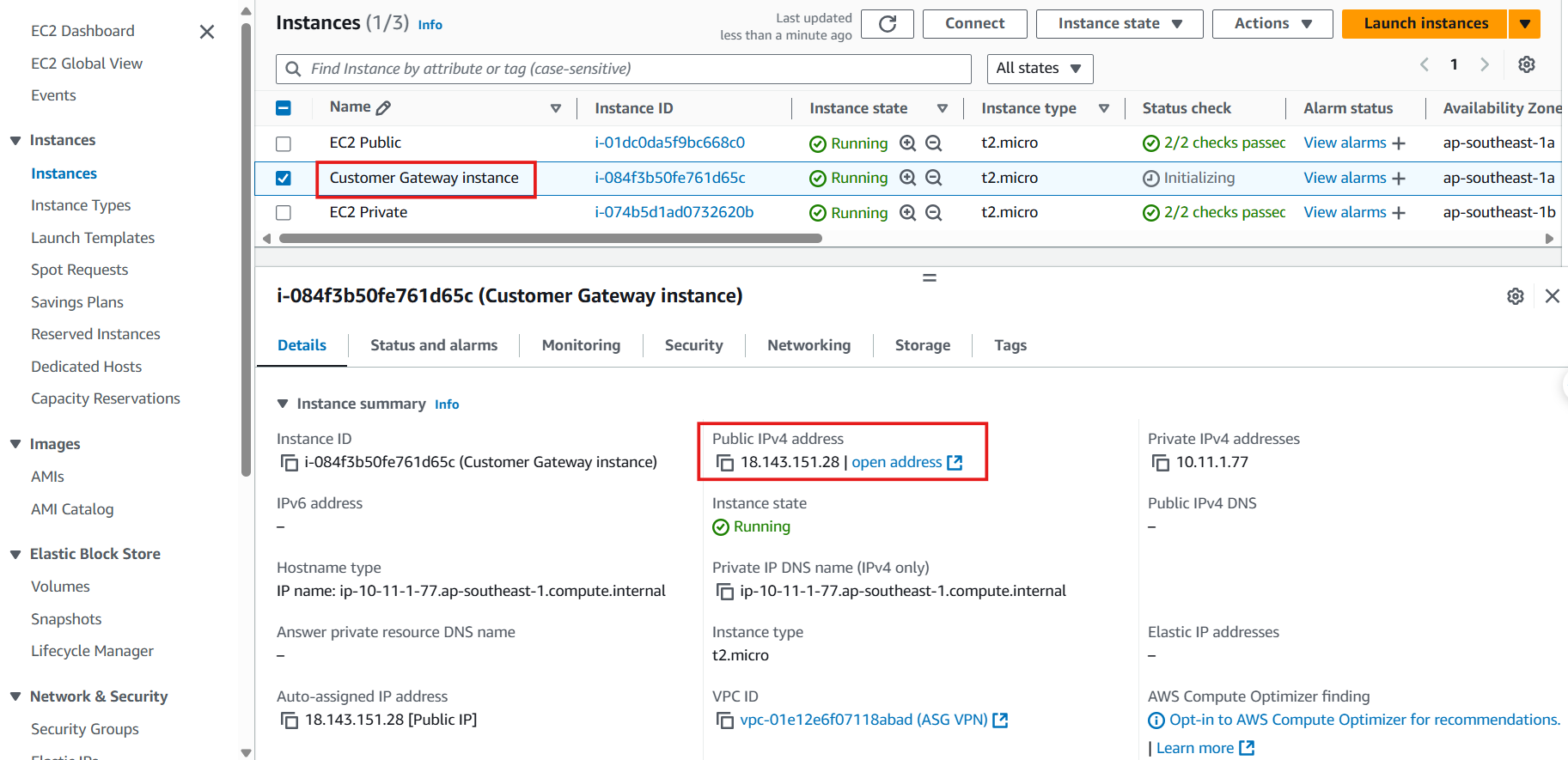
Create EC2 as a Customer Gateway
Create EC2 as a Customer Gateway
-
Access to VPC
- Select Security Group
- Select Create security group
-
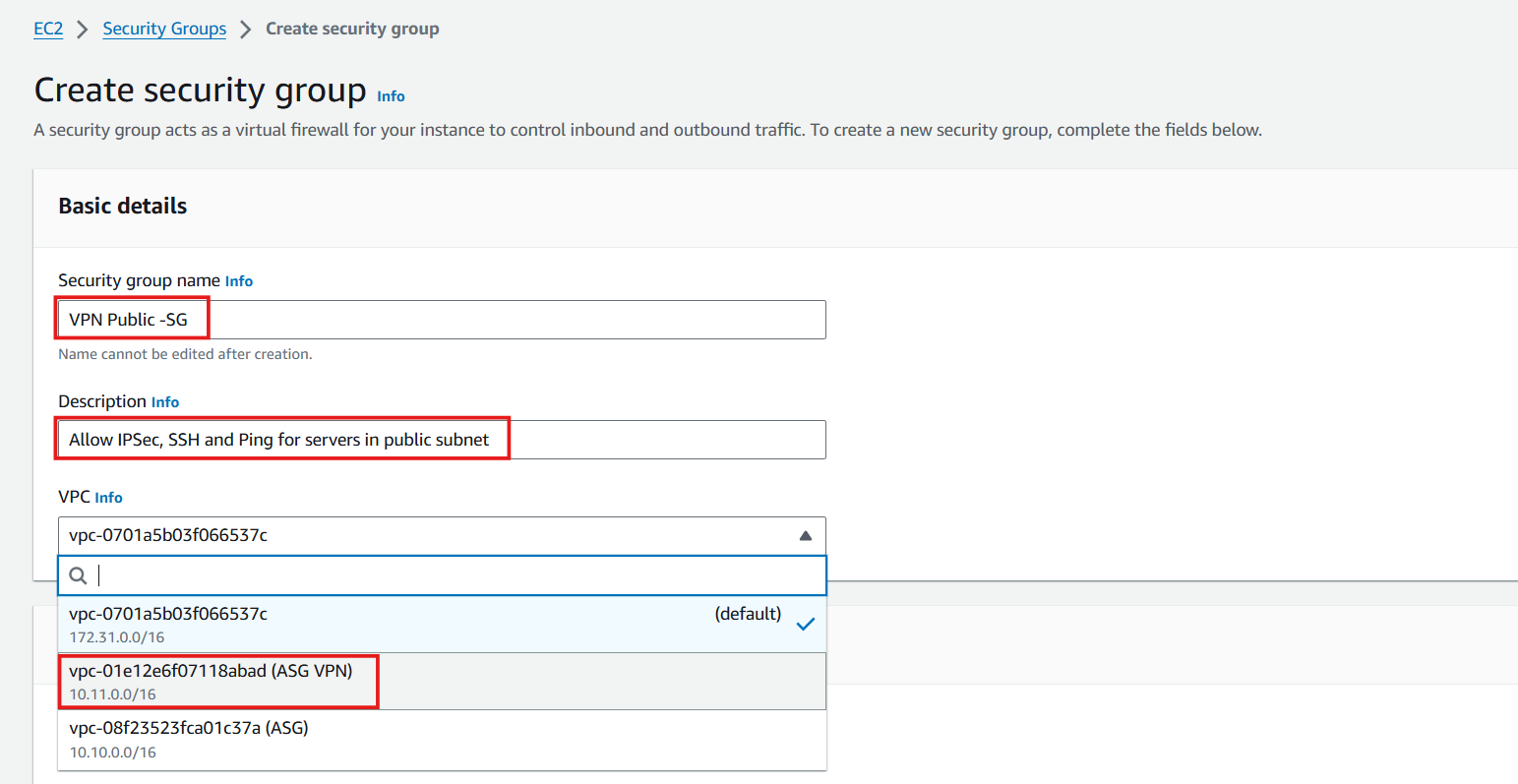
In the Create security group interface
- Security group name: Enter
VPN Public -SG - Description: Allow IPSec, SSH, and Ping for servers in the public subnet.
- VPC: Select ASG VPN VPC
- Security group name: Enter
-
Configure Inbound rules
- Select Add rule
- Type: SSH, Source: My IP (Your public IPv4 address).
- Click Add rule to add a new rule.
- Type: All ICMP IPv4, Source: Anywhere (Allow ping from any IP address).
- Click Add rule to add a new rule.
- Type: Custom UDP, Port: 400, Source: Anywhere.
- Click Add rule to add a new rule.
- Type: Custom TCP, Port: 500, Source: Anywhere.
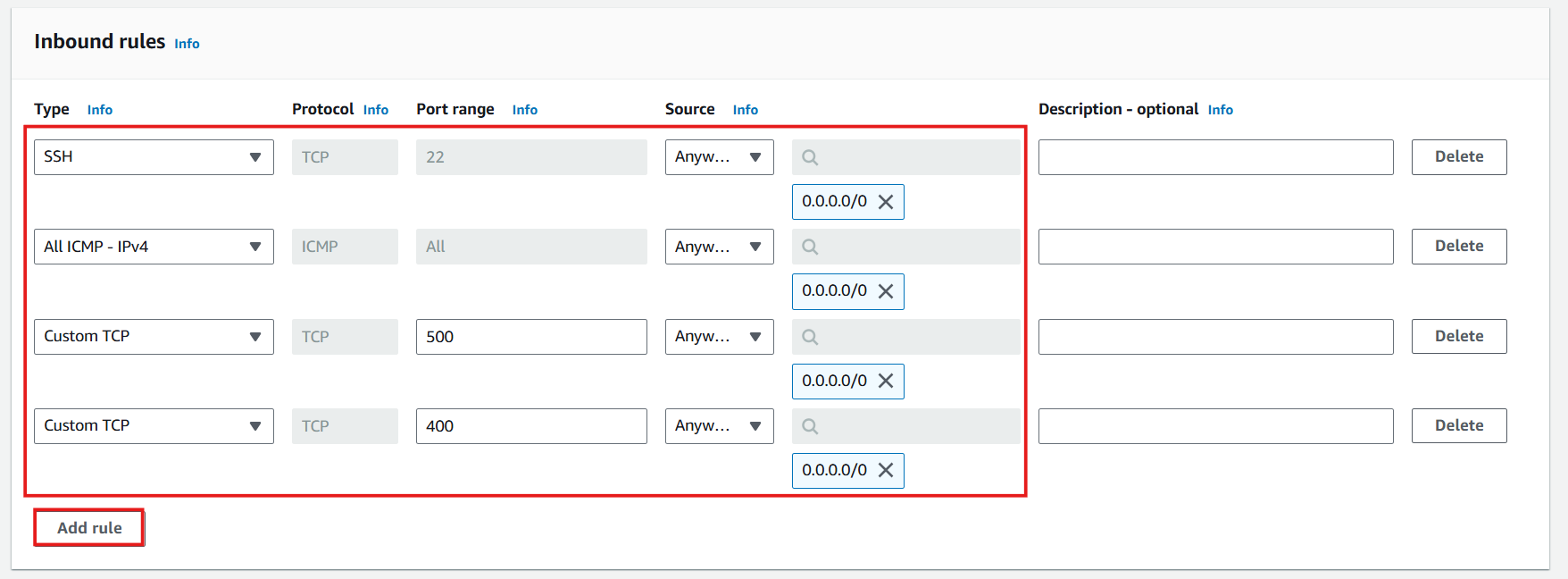
- Check Outbound rules and select Create security group
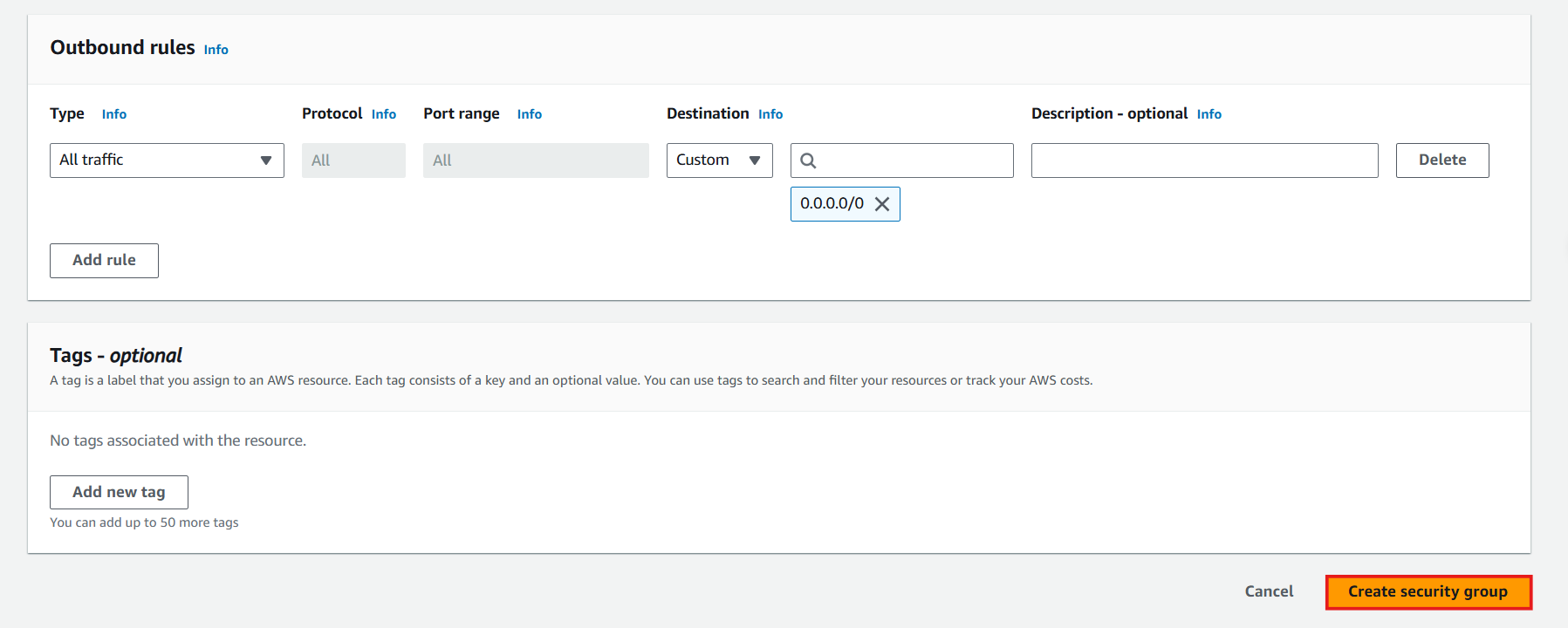
- Complete the creation of VPN Public - SG. A Security Group has been created. Next, we will proceed to create an EC2 server that plays the Customer Gateway role.
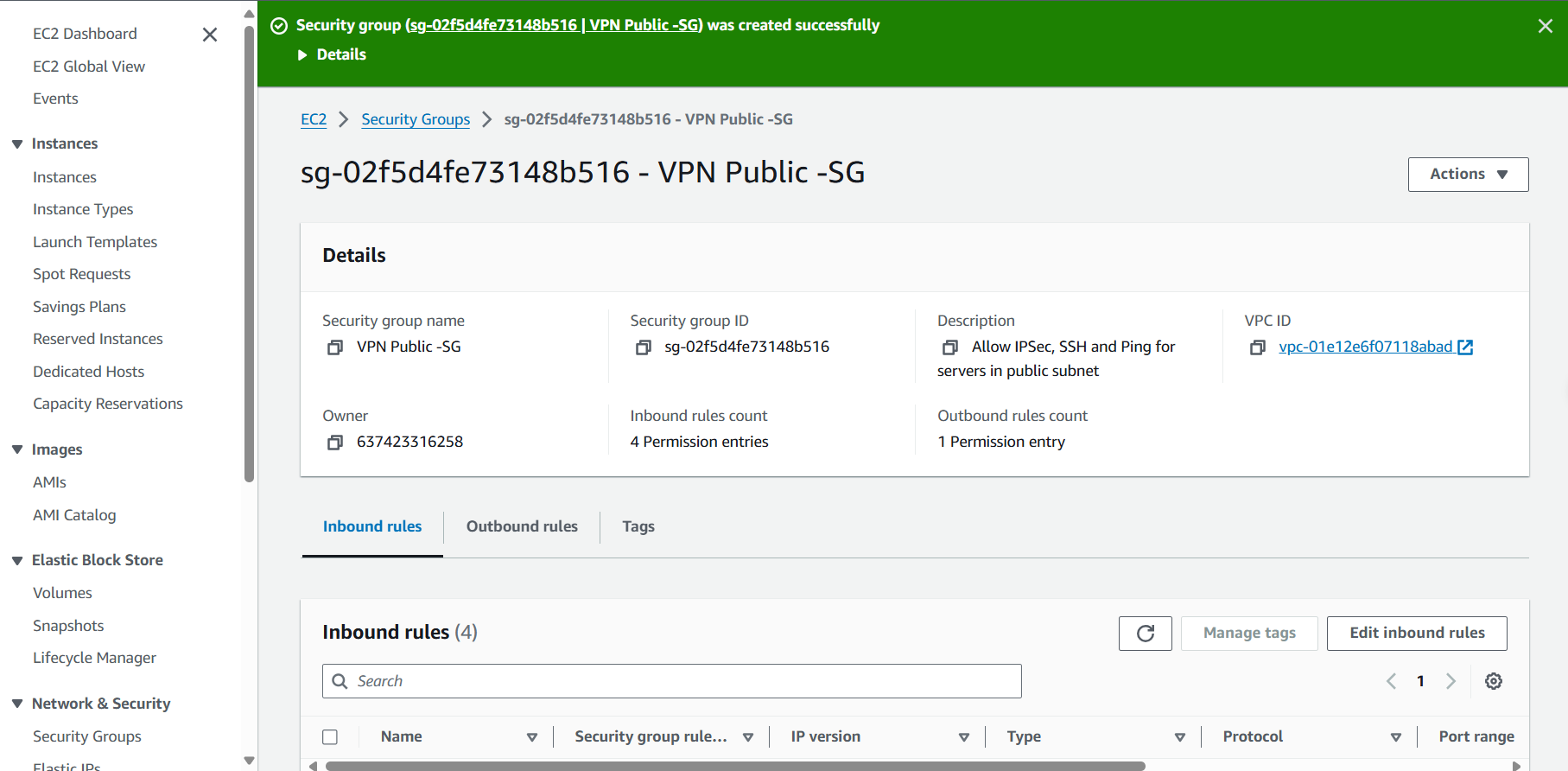
-
Access to EC2
- Select Instances
- Select Launch instances
-
In the Launch instances interface
- Name: Enter
Customer Gateway instance
- Name: Enter
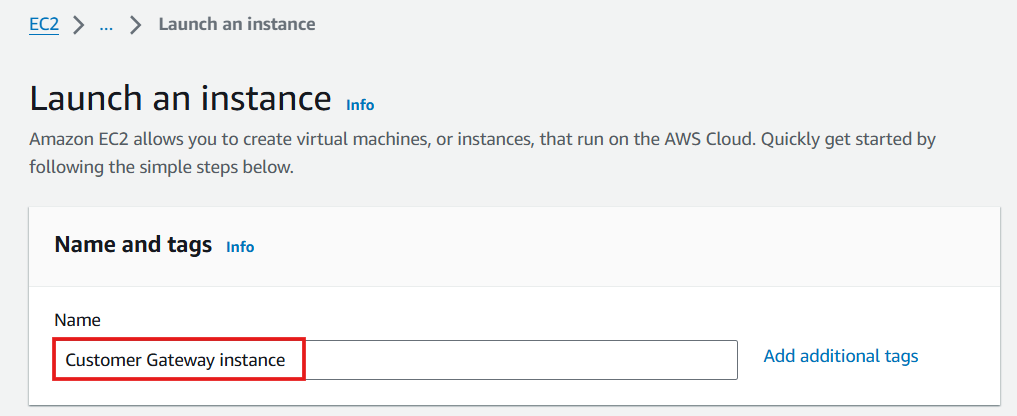
-
Executing AMI Selection
- Select Quick Start
- Select Amazon Linux
- Select AMI
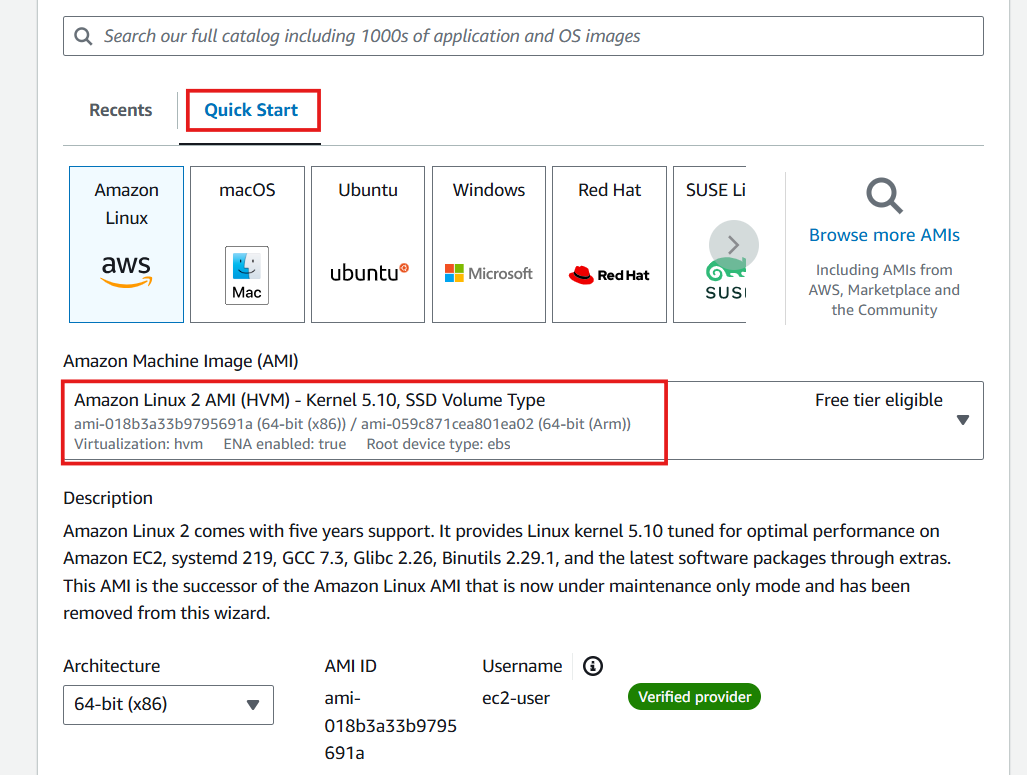
- Select Instance type and select Key pair: aws-keypair (keypair created with instances)
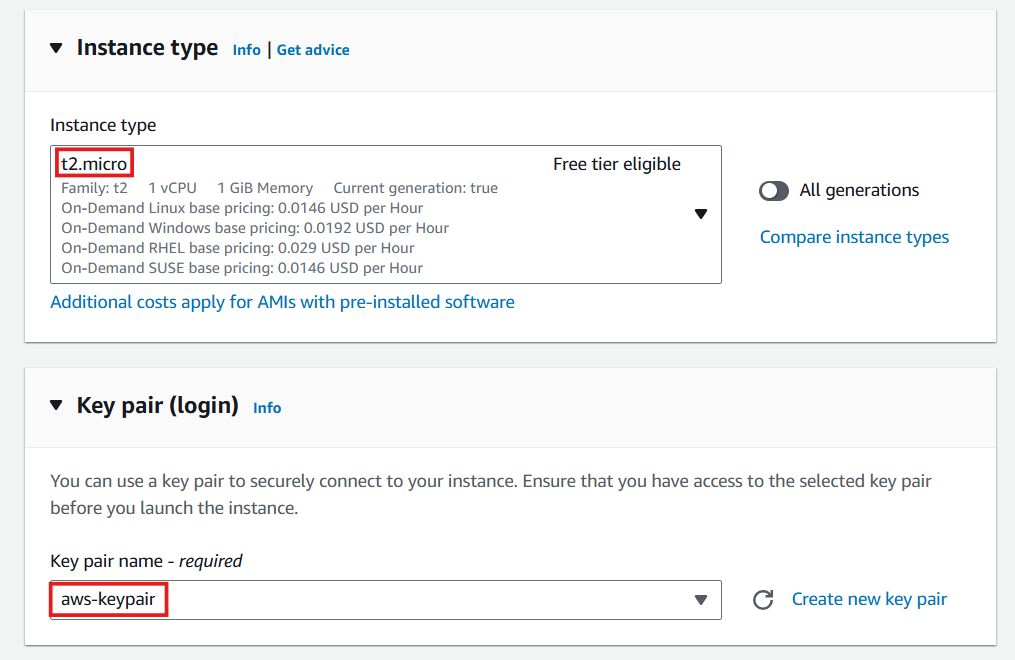
-
Configure Network
- VPC: Select ASG VPN VPC
- Subnet: Select VPN Public
- Auto-assign public IP: Select Enable
- Firewall: Select Select existing security group
- Select VPN Public - SG
- Check again and select Launch instance
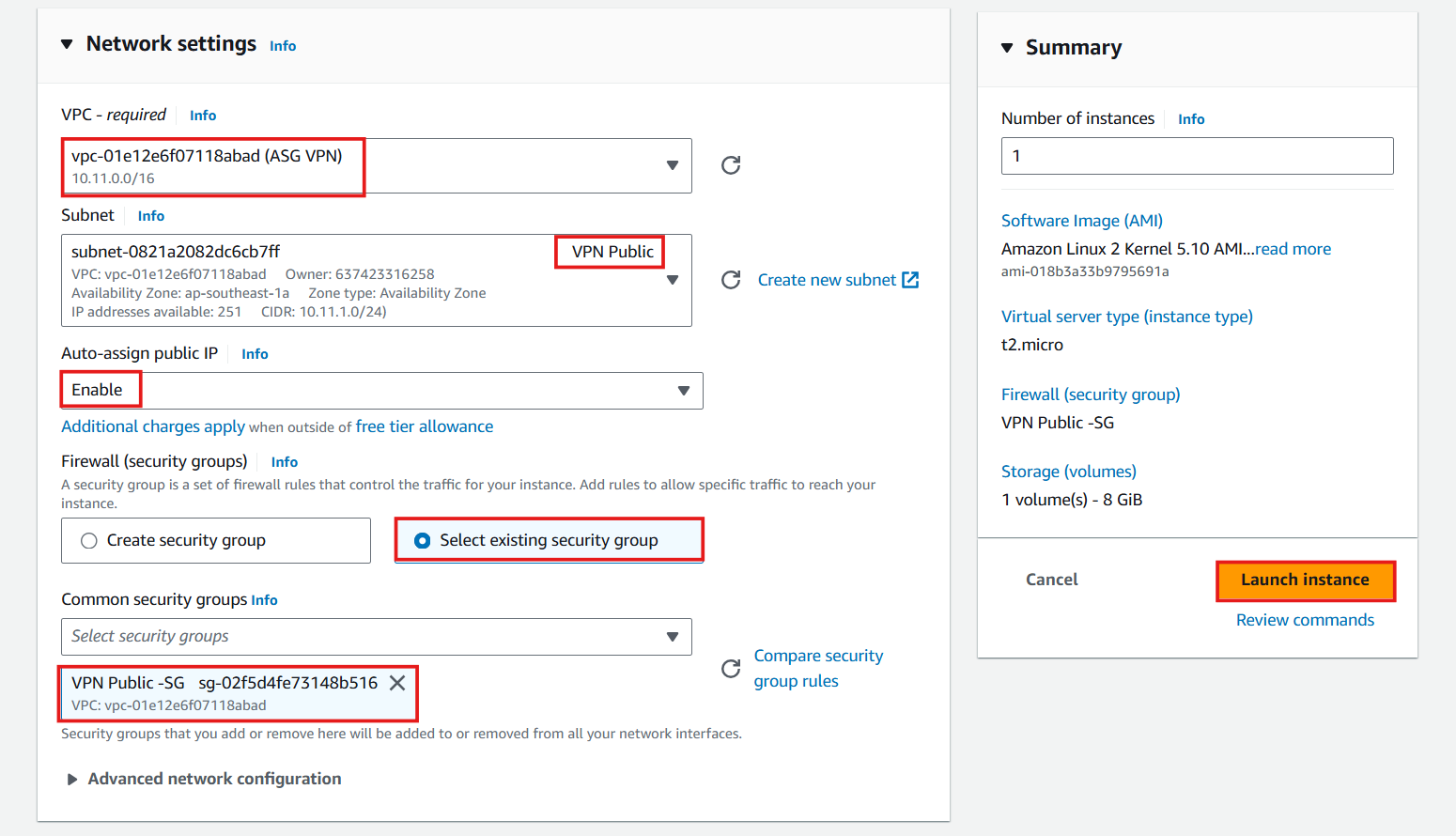
-
Finish creating the EC2 instance
- Select View all instances
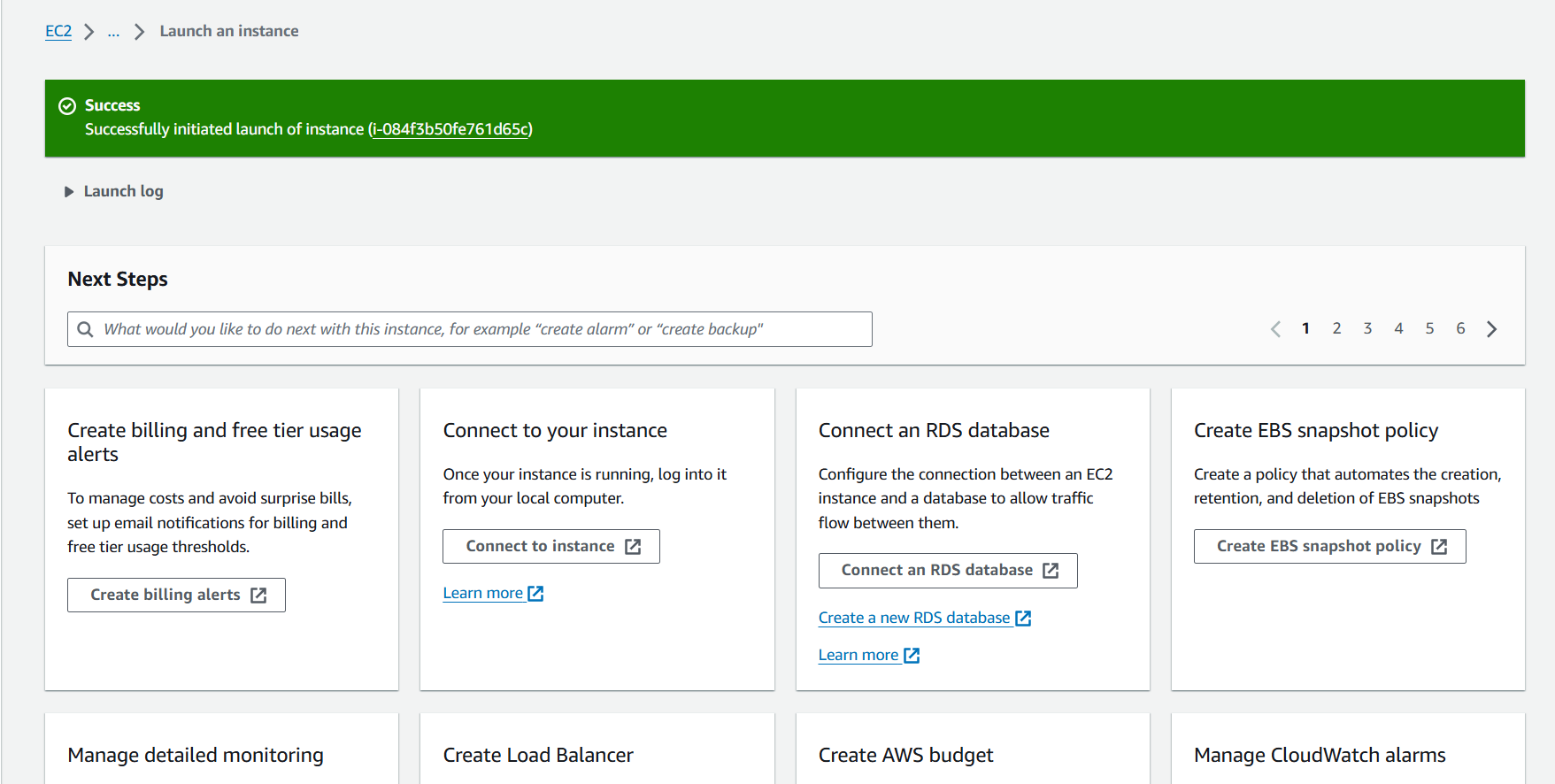
- View details of the Customer Gateway instance